
Brian Sims
Editor

Brian Sims
Editor
Ellie Hurst explains the difference between disaster recovery and business continuity and why testing these plans is essential to keeping businesses operational
DISASTER-RECOVERY (DR) and business-continuity (BC) planning are part of overall resilience measures. Building resilience by drafting a good-quality BC plan and testing it against a realistic risk assessment is never time wasted and could well reduce the chances of your business entering the last-chance saloon that is disaster recovery.
Often, the latter is confused with business continuity and, although it is also important as part of resilience, the role of DR is very different. As the name implies, it is a response to something that has already happened, not a preventative control, or mitigation of a situation that could bring about an interruption to business. Often, it is devolved as a project to the IT Department, and ends up effectively just being ITDR, with IT systems prioritised, as if the only necessity is to get IT systems back working. The people required to run or use them may not even have been considered as part of the plan. So, the plan is really only about recovering the IT systems and not the business. DR and BC are both people-centric processes, so forgetting people, the impact on people, or how people work as part of the business can mean the difference between effective DR and failure.
DR tends to get a lot of focus, mainly because it is conflated with BC. Both are perceived as IT-centric issues that can potentially be solved by an easy software solution. They can’t, of course, but efforts to keep business moving and pre-empt the most common disasters are growing. The reported increase, according to the Business Continuity Institute (BCI), in the percentage of businesses looking to comply with, or certify to ISO 22301, the de-facto business continuity standard1, would seem to bear this out.
How businesses approach BC can also depend on the sector in which they operate and the nature of the work they do. The priority of service-based companies, for example, may well be the provision of service to their customers, rather than their ability to recover themselves. For such companies, having a DR plan in place that ensures the data centre is able to ‘IT’ recover but that does not address the inability of staff to get to work because of other interruptions is not much help, because the business cannot genuinely continue. It will fail to recover, even though, on the face of it, there is a DR plan in place.
In a threat landscape that is constantly shifting, and given the seemingly unending variety of factors to deal with, how are businesses considering these potential disrupters in their plans and thinking? The aforementioned BCI report highlights the gaps that exist in some cases between perception and reality when it comes to threat. It is also clear that the connected world simultaneously enables and disables our ‘business as usual’ capabilities.
Lessons learned
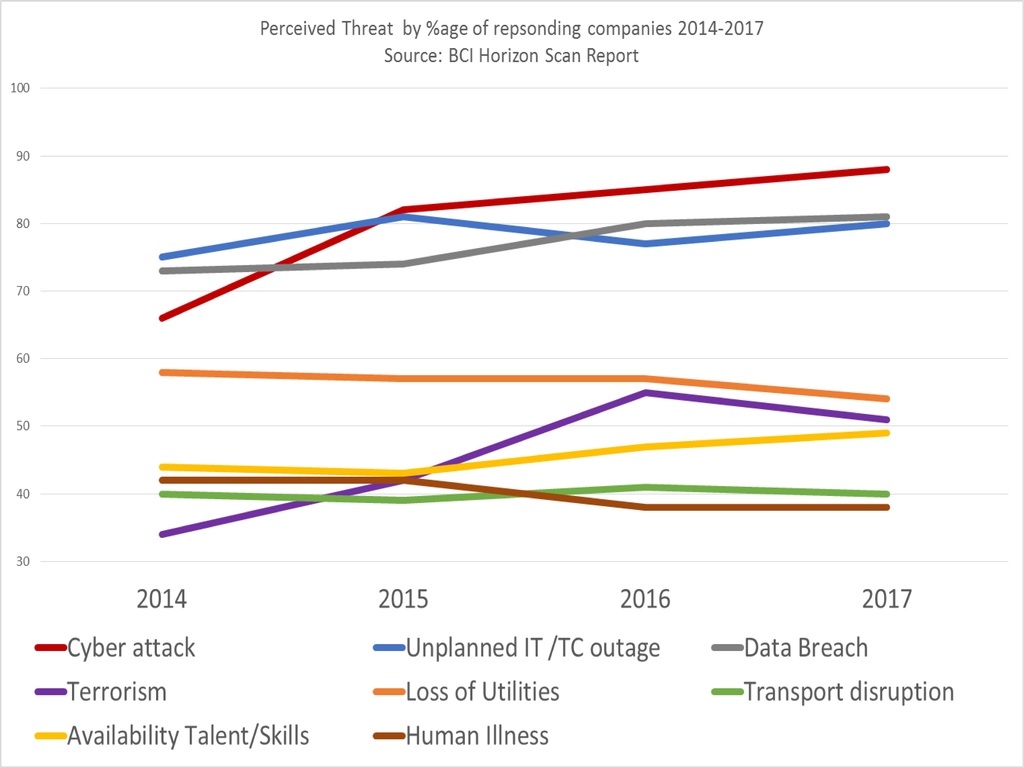
We can learn a lot from what goes wrong and what remains undone in DR to enhance BC planning. This may sound obvious, but looking at the BCI statistics relating to perceived threat and actual incident (see Figure 1), it sometimes seems that some businesses are more prepared for a terrorist attack (51% showed an elevated level of concern in the last BCI survey) than transport network interruptions (40%). Despite the high profile that terrorist attacks receive in the press, they are, fortunately, still relatively rare, while transport network interruptions are much more common.
Perception needs to be managed, and a proper risk methodology is also required to ensure resources and attention are focused on the right areas so that risks are managed in a proportionate, pragmatic and cost-effective manner. Recovering from an unexpected disaster is incredibly challenging. Some businesses do not ever recover; research has shown that up to 60% of smaller businesses that suffer a cyber-attack fail to survive beyond the six-month mark, for instance. That is very worrying for the UK, where more than 95% of businesses can be classed as small.
Figure 1 reveals that concerns about cyber-attack, data breach and IT outage consistently outweigh those relating to human illness, talent or skill shortages, and availability of utilities or transport. So, you may recover IT services only to find yourself thwarted by failure to plan for illness, or lack or running water/sewage services, or a transport disruption that prevents your people from getting to work and using the IT system, diligently recovered. It could be argued that the advent of more flexible working arrangements and possibilities have caused the drop in concern over such issues, but as these data are drawn from threat perception and not from risk-based results, this cannot be asserted conclusively.
As in the case of terrorism, media focus on cyber-attacks also undoubtedly contributes to the perception by businesses that they are having to deal with more cyber-related issues and threats. Certainly, the recent spate of ransomware attacks has served to increase business concern in this area. The huge skills shortage in cyber-security circles, which, the ONS predicts, may last a generation, is adding to the problem.
Technological advances
Every day, we connect more and more sensors, platforms and devices to the Internet. It has been suggested that something like a quadrillion devices are now hooked up to it and woven through our business and home structures, as well as our supply chains. This opens us up to attack and exploitation in innumerable ways, many of which we don’t even know or understand yet.
While we were busily web-enabling our sports clothing, kettles and fridges, along came ransomware like WannaCrypt, WannaCry and Petya and showed us what can happen to all those wonderful insecure devices. The Mirai botnet captured, among other things, millions of unsecured security systems and turned them into a virtual zombie army that knocked out services like PayPal and Twitter. We are still seeing the resulting chaos from some of these attacks. The impact on business is undeniable and, certainly with ransomware, it is growing. In fact, in BC terms, or at least according to the definitions of the BCI reports, it could fall into the top two categories, as it is a form of cyber assault but it is also an interruption to IT services, effectively locking up networks, preventing user access, or encrypting files to prevent use.
Like most effective malware, though, it relies on humans to download the file that causes the infection. There are many technical back-ups businesses can have in place to try to prevent infection but well-trained people will always be the best first response. We need to make sure we consider both the risk and the benefit of employees, however. Technical solutions that don’t consider the human factor will not be enough to mitigate the risk the latter represents. Indeed, humans are the random, unpredictable factor that can introduce the risk in the first place.
When it comes to business continuity, the risk-based approach to planning is the most effective. It will ensure focus is placed where the risk is real, the consequences are considered and mitigation measures are tested and kept up to date. If we leave out the human factor and rely on ITDR, we miss huge opportunities to build organisational resilience and are potentially ignoring very real risk.
Ellie Hurst is marcomm and media manager at Advent IM Ltd
References


Unit 5
Coombswood Court
Steelpark Rd
Halesowen
B62 8BF
UNITED KINGDOM
0121 559 6699